NotPetya Attack
NotPetya was a large scale attack aimed at Ukraine in 2017, its damage was monstrous, causing an estimated $10 billion dollars of fiscal damages, affecting roughly 2300 organizations in over 100 countries. How did this attack happen and what lessons were learned? Continue reading for an analysis of one of the largest cyber attacks of all time.
A brief History
Petya is a family of encryption based malware used to target windows machines, First discovered around 2016. It functioned by locking users out from their data and requested a ransom payment to be made for the disk to be accessible again. It spread through malicious email attachments and the origins of the malware still remain unclear since it was overshadowed a year later by its vastly more deadly, modified variant called NotPetya.
On April 14th, 2017, The United States National Security Agency (NSA) is hacked and an exploit code named EternalBlue is stolen. This exploit had been used in intelligence gathering and counter terroism missions, through exploting vulnrabilities in the Microsoft operating system. However after the leak from the NSA, Microsoft quietly patched the vulnrability.
A cyber threat actor group known as the Shadow Brokers had taken EternalBlue into their own hands and the sysadmins responsible for the attack were not prepared for what came next.
NotPetya comes from the same group of ransomware malware originating from EternalBlue and it had some key technical differences from Petya including:
- Locking the entire disk instead of the master file table(MFT).
- Self replicated and infected machines on the same network using EternalBlues network exploits.
Petya was relatively harmless, it asked for $300 dollars in bitcoin, required emails to spread it and gained little traction. Its newer variant which utilised a nation state developed exploit, shook the world.

Inner Workings
NotPetya had many moving parts which made itself infinitely more deadly. It had a ransomeware component which locked down the machines and its spreading mechanism powered by Eternal Blue.
Spread
There were a handful of methods used by the exploit to spread throughout networks, a key point here is that it spread through networks, not across external networks. The attack was good at crippling and disabling businesses after the infection had taken place.
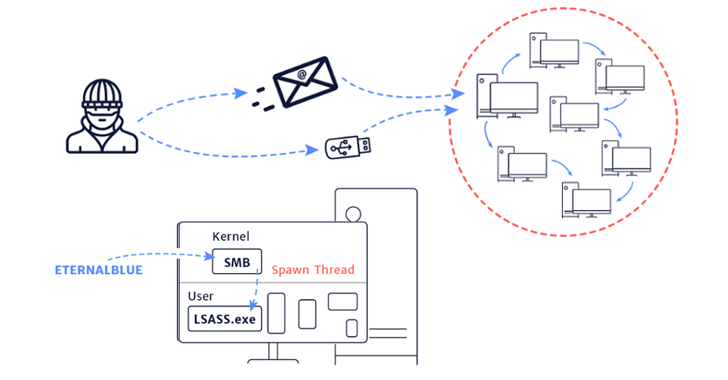
Windows machines utilise the Server Message Block (SMB) protocol for network attached storage. The earlier version 1(V1) had a vulnerability which the NSA had abused to spread malware through remote code exectution. By using modified data packets, an infected machine would send the malware across the network to all other machines it could reach.
Payload
The payload contained by the attack was lethal, it featured the ability for the attacker to steal credentials, gain admin rights to the machine and finally encrypt the disk.
Once the malware lands on the machine, it firstly encrypts the master boot record by overwriting its config with its own malicious one. Sometime after, NotPetya will try to force the machine to error, causing the system to restart, leading to the user finding out they have been infecting. As a contingency, the malware also set a restart task, incase the error to restart method did not work as intended.
Targets
The attack had primarily targeted Ukraine, with the first infection being reported to have first appeared at a telecomms company which serviced one of the largest banks in the country. The state-owned Oschadbank, with over 3600 branches and 2850 ATM machines. The attack was devastating however, this was only the beginning. Below is breakdown from a select few of the targets which affected the way the world moved forward, from the almost 2300 which had been hit.
Maersk
A Danish multi-national logistics company was infected through their office in Ukraine. Their entire global network was soon infected as the malware spread from machine to machine. Since the companies network was not segregated by region, the flat network offered little resistance to the malware making them completely vulnerable. It was only a matter of moments from the point of infection, to their global business being brought to a halt, the attack had crippled their systems which controlled bookings, meaning ships could not dock at their 76 ports and shipping docks. The company were forced to take their entire infrastructure offline in order to rebuild. They had a stroke of luck however when they discovered that a single server had been offline during the incident.
4000 servers, 45,000 computers and 2500 applications had to be reinstalled, this monumental task took a total of 10 days with the support of Microsoft, this was expensive however and brought the total cost of damages to around $300 million.
Maersek themselves are worthy of their own post, given the monumental effort they had taken to restore functionality globaly so rapidly.
Merck
An American pharmaceuticals company was an interesting case study from the fallout of the attack. They are the first company to have claimed damages of cyber damages from their insurance company. However, the insurance companies denied their claims of a monumental $1.4 BILLION leading to a lengthy litigation which was only resolved in early 2024. An out of court agreement lead to a settlement of $700 million, a little under the estimated $870 in damage caused.
From disclosure of damages given to the courts, it was revealed that 10,000 machines had been taken offline within 90 seconds of the infection entering the network. A total of 40,000 machines were infected causing their mission critical infrastructure to go offline.
Their supply chain and factories had grinded to a halt, taking upwards of months to fully recover from the attack. Their vaccine production had been hit, causing the company to dip into the emergancy stockpile of HPV vaccines without being able to replenish. Furthermore, their highly automated process had to be run in manual mode by employees until their entire infrastructure was rebuilt.
Years after litigation, with insurance comapnies claiming the attack was conducted by a nation state, thus an act of war and saught to deny the claim. However the courts had disagreed and disupted that during peacetime an act of war cannot occur and without cyber specific language in their policy the definition of act of war was not sufficient enough. After this insurers such as Lloyds have since changed their language to include cyber specific language and also made their cyber policy seperate to their all in.
Mondelez
The company responsible for producing Oreos, Ritz Crackers and purchaser of Cadbury were also hit and affected. It was through court documents they had disclosed that they had lost approximately 1,700 servers and 24,000 laptops. In 2022 they too had also reached a settlement with their insurance company for a much smaller $100 million. It had taken them 5 years of battling the same reasoning as Merck for their claim denial, however private settlement was achieved and no landmark ruling was made.
The machines affected by the company were lost entirely. Without any means of recovery, it took engineers weeks to replace the damage equipment and get the business moving again.
Mondelez was forced to contain the damage to maintain brand reputation as they are seen as a global leader, owning many iconic brands. This lead them to innovate new disaster recovery plans for the future should this happen again, they have the expertise be resilient against such attack.
Lessons Learned
NotPetya was a world changing event, much more devastating then wannacry, causing the global economy to bare the brunt of the damage, even 7 years on it is still being discussed.
The attack firstly caused a dramatic increase in spending in 2018 for cybersecurity awareness, alongside disaster recovery plans and education. The aforementioned Maersk case study was used as a poster child for global conferences, spreading awareness for the need of proper network segmentation, software defined networking and offline backups. Had networks had stricter access control lists, disabled deprecated protocols such as SMB v1 and isolated their network into geographic regions. They would’ve been able to better protect themselves and their clients from the damage caused.
Companies had taken responsibility to finally value patch management, since the vulnerability had already been disclosed and patched by microsoft, it could have been prevented by using the latest operating systems version. Automated patch management, using Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) have since become valuable tools in an orgnaisations tool book to provide asset and network visibility. Through the power of automation it is hoped that if a similar attack was to happen again, it could be contained and blocked off from the rest of the network.
Terms such as Zero-Trust were heard of in the industry but without such an attack, they weren’t taken as serious but since then have become a much more common place technology within organisations. Users and devices within the network are continiously monitored and network policies such as least privilage paired with user segregation has created a much more secure environment. Proper usage of network security could have prevented billions in damages but the lesson was learned the hardway.
Futhermore work in the blockchain industry to improve cyber resilience has seen a big uptake, in particular trade, shipping and logistics. Blockchain technology helps provide an immutable and secure infrastrucutre which is decentralised. Global bodies such as the United Nations Commission on International Trade Law have introduced The Model Law on Electronic Transferable Records (MLETR), which seeks to give electronic documents the same legal authority as paper based. Enabling blockchain based documentation would have helped keep a decentralised and secure copies of paperwork which was otherwise stored in local servers that got taken down by the attack. The aim to increase cyber warfare resilience at points of key infrastructure is being taken seriously by leaders at the global level. With the Digital trade documents act being passed into law UK Parliment in September 2023, all companies and countries adhering to English Common Law in their trade policies are now able to safely store their documents and have them recognised on a decentralised network.
Secondly it was a wake up call to policy makers and insurance companies. Never before had such an attack at this unprecedented scale taken place. Thus there was a swift action for those on the covering end and also the bodies responsible for ensuring proper handling of business information systems. Insurance companies were all paying attention the case with Merck, no one wants to find themselves on the receiving end of the attack, thus there was a wave of policy changes to include cyber specific language across the industry.
references
Maersk case study - https://www.sipa.columbia.edu/sites/default/files/2022-11/NotPetya%20Final.pdf
Lessons Learned 6 years on - https://www.infosecurityeurope.com/en-gb/blog/threat-vectors/learnings-from-notpetya-cyberattack.html
What is EternalBlue- https://www.avast.com/c-eternalblue
Yale case study of past and future harm- http://www.cs.yale.edu/homes/jf/rudderkelly_87056_5809038_CPSC_610_Final_Paper.pdf
What is Petya and NotPetya? - https://www.cloudflare.com/en-gb/learning/security/ransomware/petya-notpetya-ransomware/
Merck lessons learned - https://www.strategic-risk-global.com/cyber-/-technology-risks/lessons-from-mercks-notpetya-victory/1440095.article
Mondelez insurance case study - https://www.sciencedirect.com/science/article/abs/pii/S0007681321001361
Untold Story of NotPetya - https://www.wired.com/story/notpetya-cyberattack-ukraine-russia-code-crashed-the-world/